Risk Management Enterprise - The Facts
Wiki Article
The smart Trick of Risk Management Enterprise That Nobody is Talking About
Table of ContentsRisk Management Enterprise Fundamentals ExplainedThe Risk Management Enterprise IdeasThe 6-Minute Rule for Risk Management Enterprise
Control who can watch or modify these aspects by setting particular access rights for specific customers, making certain info safety and security and tailored usability. Permits individuals to tailor their interface by picking and preparing essential information components. Supplies an individualized experience by enabling customization of where and how information elements are presented.It allows access to real-time incorporated data immediately. Facilities can utilize detailed data knowledge for quicker and more educated decision-making.
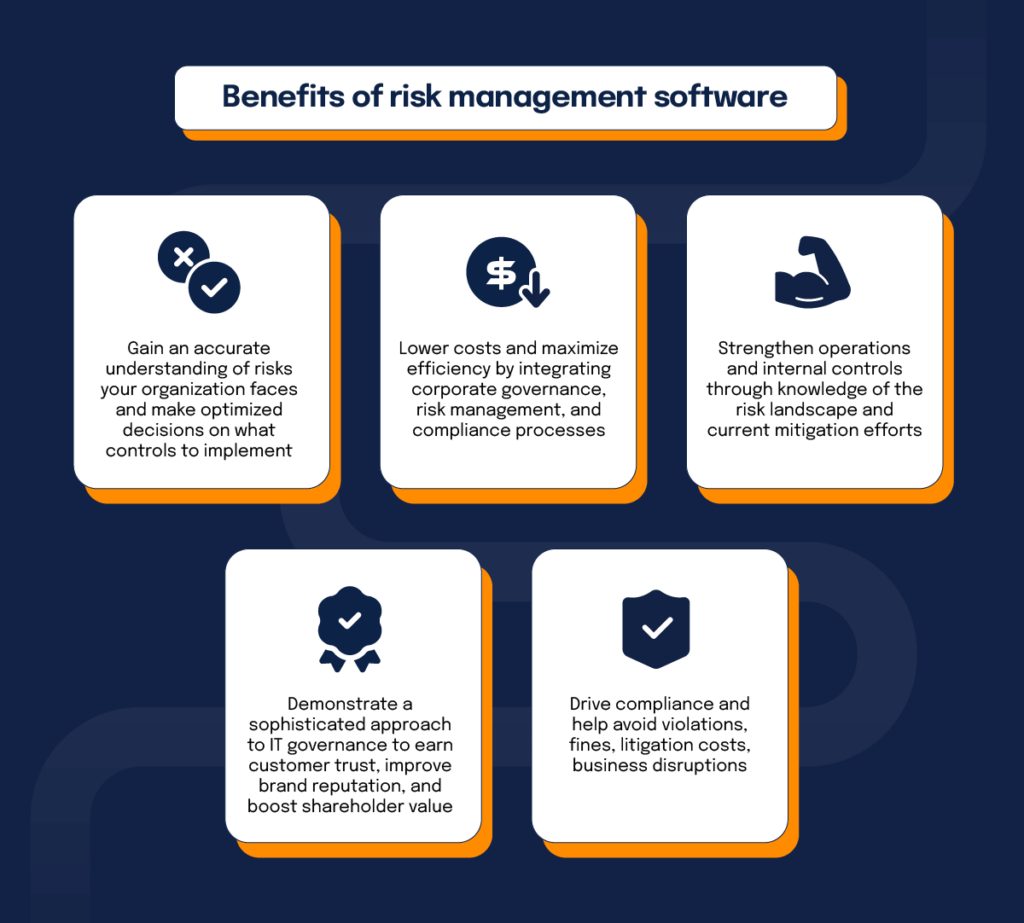

Diligent is a danger monitoring software that enables maximizing performance, and improves development. It also aids check dangers with ERM software application that consists of integrated analytics and adapts to your service demands.
Some Known Details About Risk Management Enterprise
Streamlines the procedure of collecting risk information from different parts of the company. Supplies leadership and the board with real-time threat understandings. Use ACL's innovative analytics to identify risk patterns and predict hazards.This permits firms to catch risk understandings and red flags in the third-party vendor's security record. Enables business to capture and record risk understandings and red flags try this out in third-party vendor safety reports.
It also decreases risk via structured conformity and threat monitoring. It can assist gather and track all your risks in the Hyperproof risk register.
It guarantees that everything is organized and available for auditors. Utilizes automation to maintain proof current while reducing manual initiative. It gives fast accessibility to necessary information and documentation. This guarantees the protection of Active evidence circumstances browse around here by from this source making it possible for multi-factor verification (MFA) using authenticator apps such as Google Authenticator, Microsoft Authenticator, or Authy.
The 45-Second Trick For Risk Management Enterprise
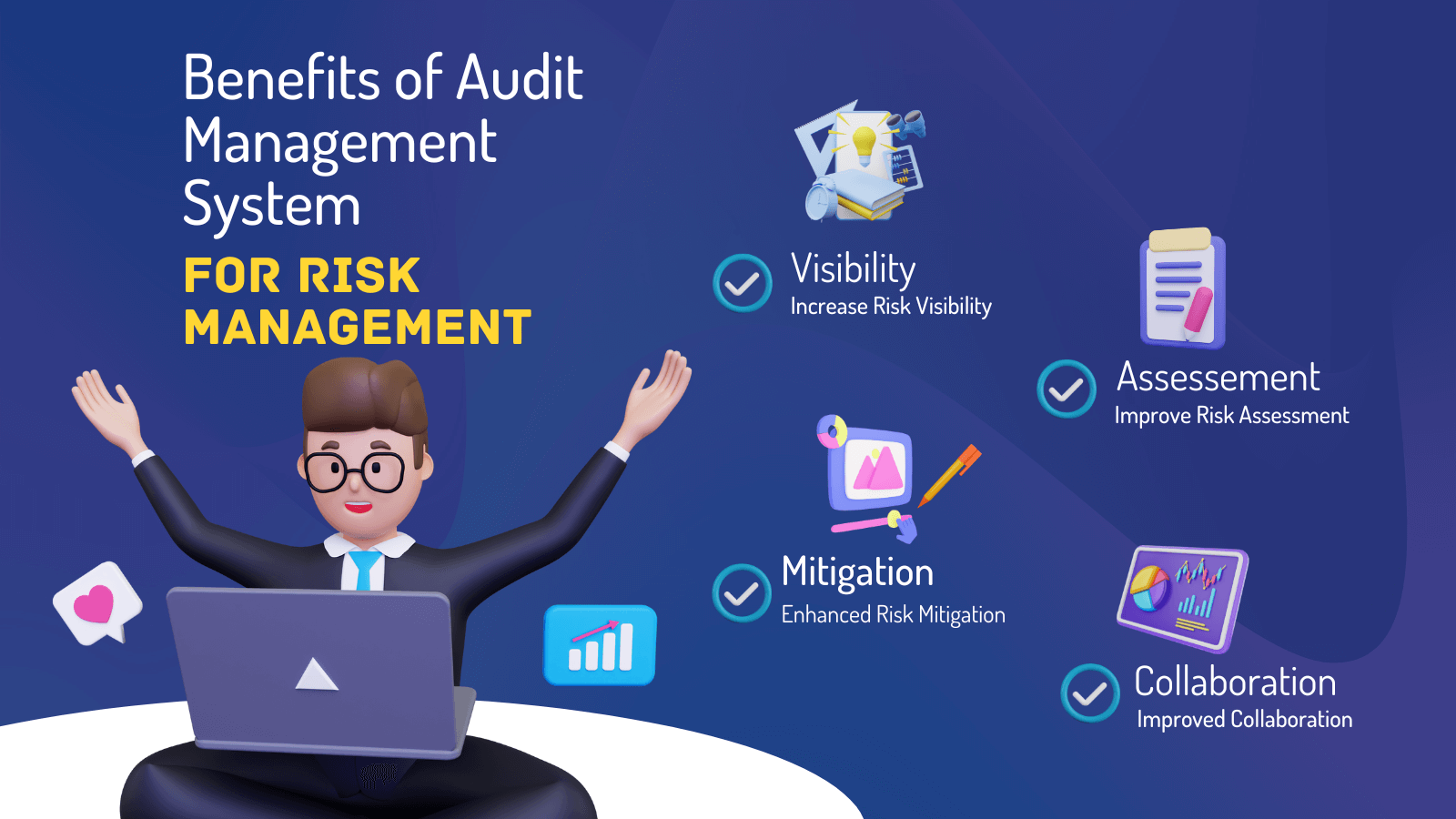
It provides top-tier security attributes to secure sensitive information. This danger management software program is an ideal device for facilities looking to deal with unnecessary concerns or dangers.
Users can likewise make use of the AI-powered devices and pre-existing web content to create, evaluate, prioritize, and address threats effectively. Streamlines the process of setting up and populating danger signs up. Uses AI and collection content to boost danger assessment precision. It makes it possible for quicker recognition and mitigation of dangers, This is mostly a visual design.
Report this wiki page